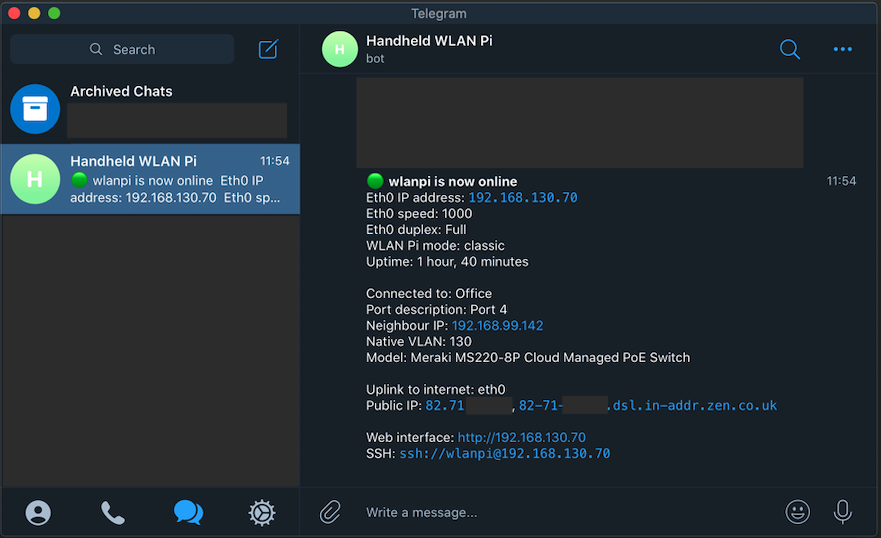
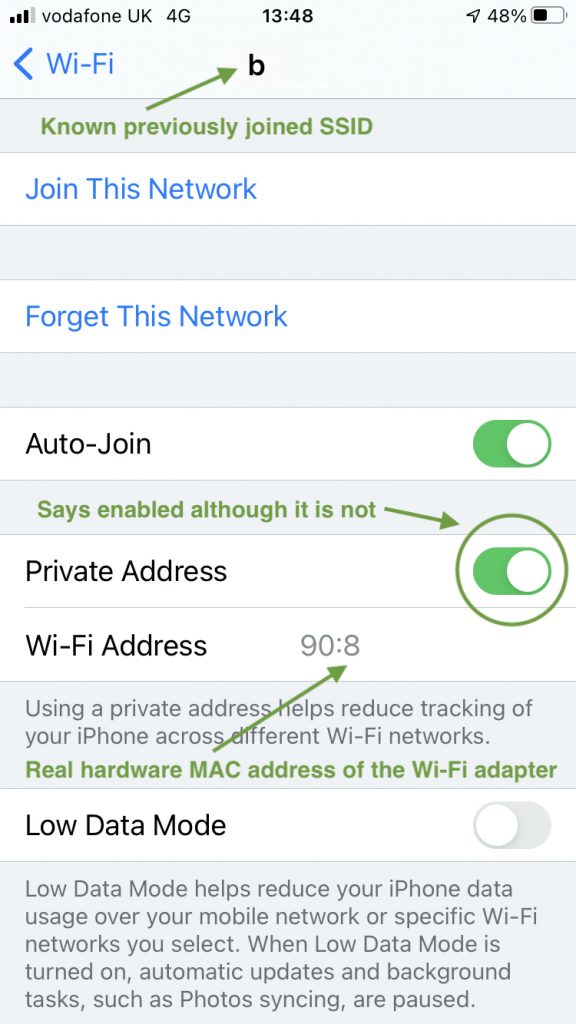
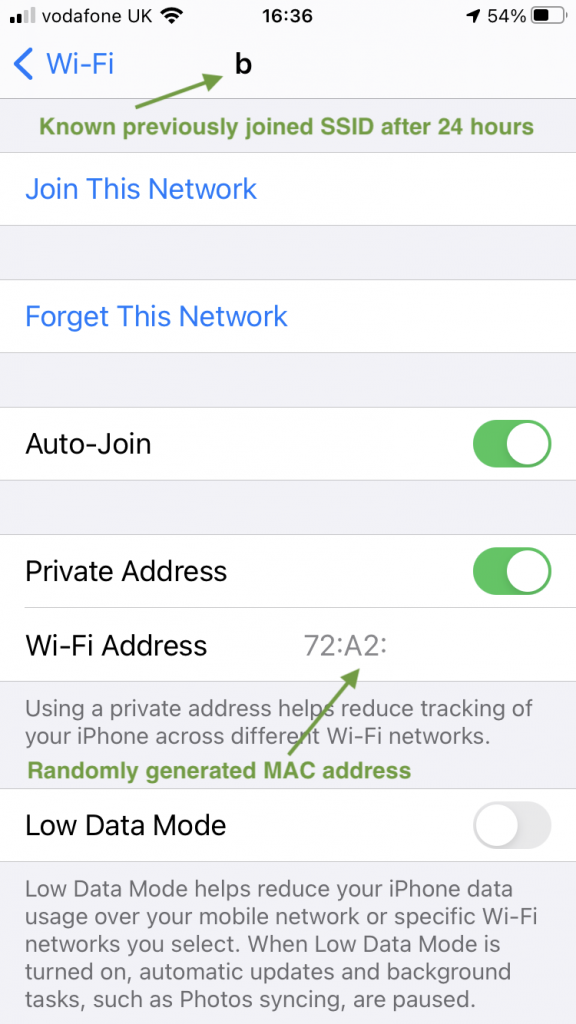
I needed to find a solution to swapping multiple outdoor AP and antenna combinations on the same tripod. Specifically MR86 with MA-ANT-20 dipoles and MR86 with two MA-ANT-25 directional antennas. Quick swapping was a key requirement. Some coverage areas required directional pattern while other locations with low traffic and low client density would really benefit from omnidirectional coverage.
MRs ship with standard pole mounting hardware, which is great for permanent installation, but it didn’t allow fast swapping of the AP and antenna sets. Also, pole mounting kit requires tools, which is not practical as it add additional weight to your survey backpack.
Please excuse the DYI approach. I did this during UK’s second COVID-19 lockdown. Shops were closed, tools were limited and I had no access to my lab.
You are smart people, so I don’t need to stress this point, but please don’t take this write-up as Cisco’s official guide or recommendation. This is just me trying to find a solution to a problem.
So, what’s the solution?
Let me show you the final adapter and we can then look into the detail.


Under the hood
It all started when I spotted my wife’s aluminium 16 mm gardening tubes;-) I realised they were perfect fit for my tripod. They slide nicely inside the top tripod tube about a couple of inches (5 cm) or so.




What would I improve?
If I were to build a second iteration of this adapter, I would add a safety wire and attach the AP mounting bracket to the tripod. I would call this mandatory, especially if you are not the only user of these adapters or if there is going to be a person stood underneath the tripod.

Apart from that, it works really well, it is rock-solid, and allows me to swap the MR with omnis and MR with directional antennas in less than 10 seconds.