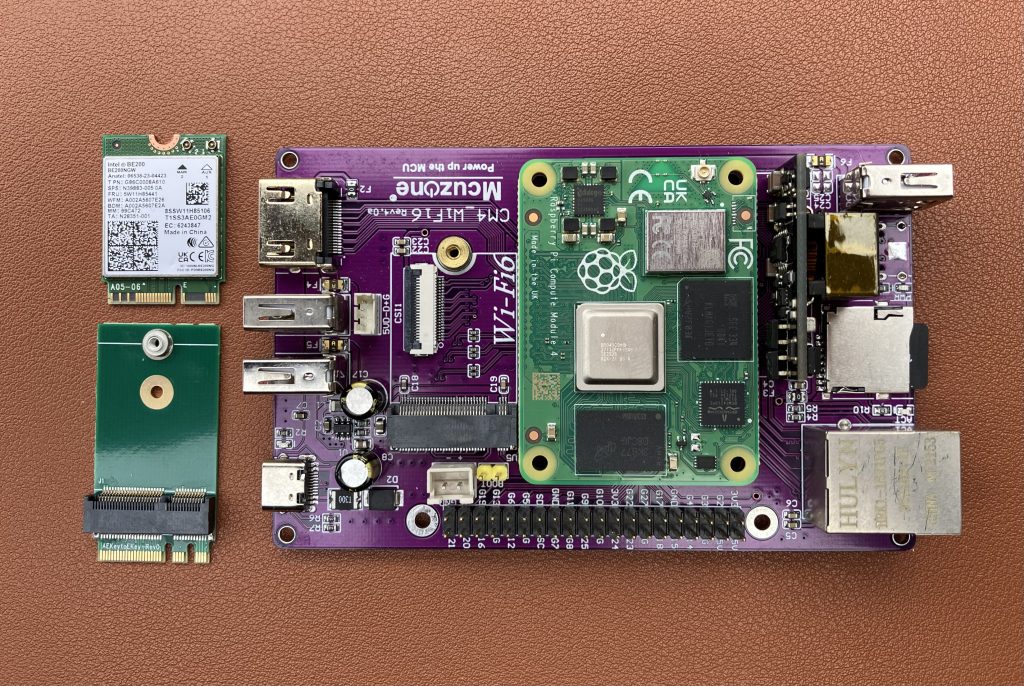
Raspberry Pi 5 comes with PCI Express connection and a number of HATs (hardware attached on top) and Bottoms (the opposite of that) are now available for sale. That unlocks some very exciting options. Let’s see how fast can a 10 Gigabit Ethernet adapter on Raspberry Pi 5 go, shall we?
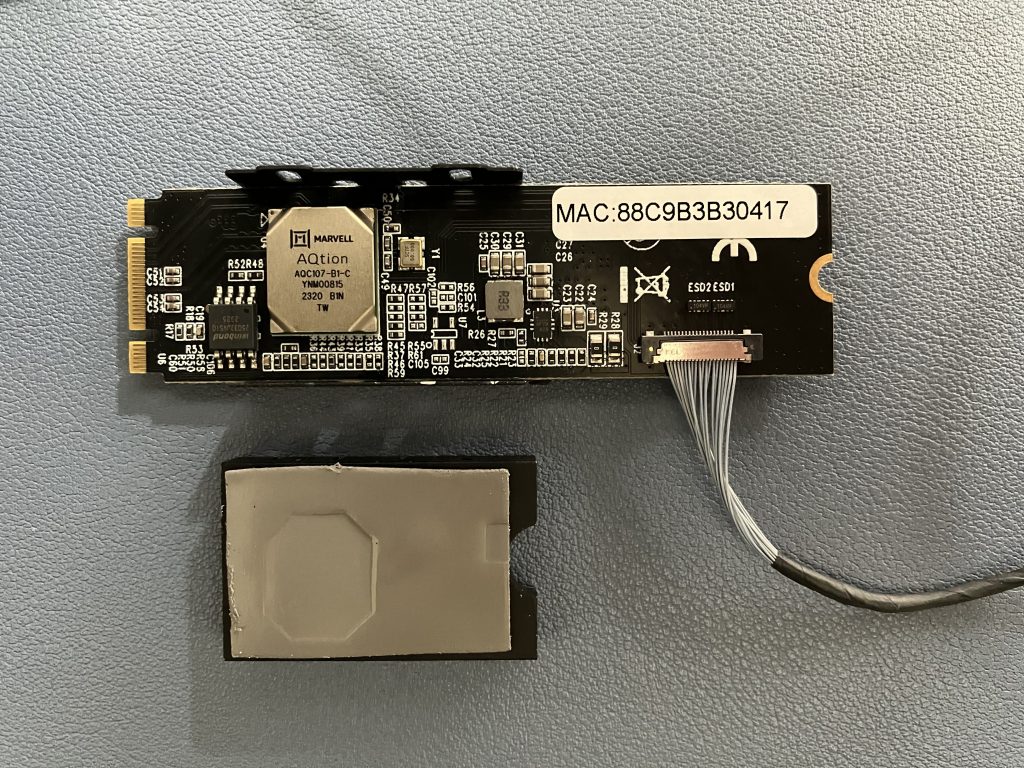
Pineberry’s HatDrive! Bottom proved to be really handy for converting Pi’s PCIe connection to M.2 M-key format. My Kalea-Informatique 10 Gigabit adapter uses exactly that, so that’s a match. Why did I choose this adapter? Very unscientifically this time – it was the first readily available and I was in a fail-fast mood :)


Enable PCIe port on Raspberry Pi 5
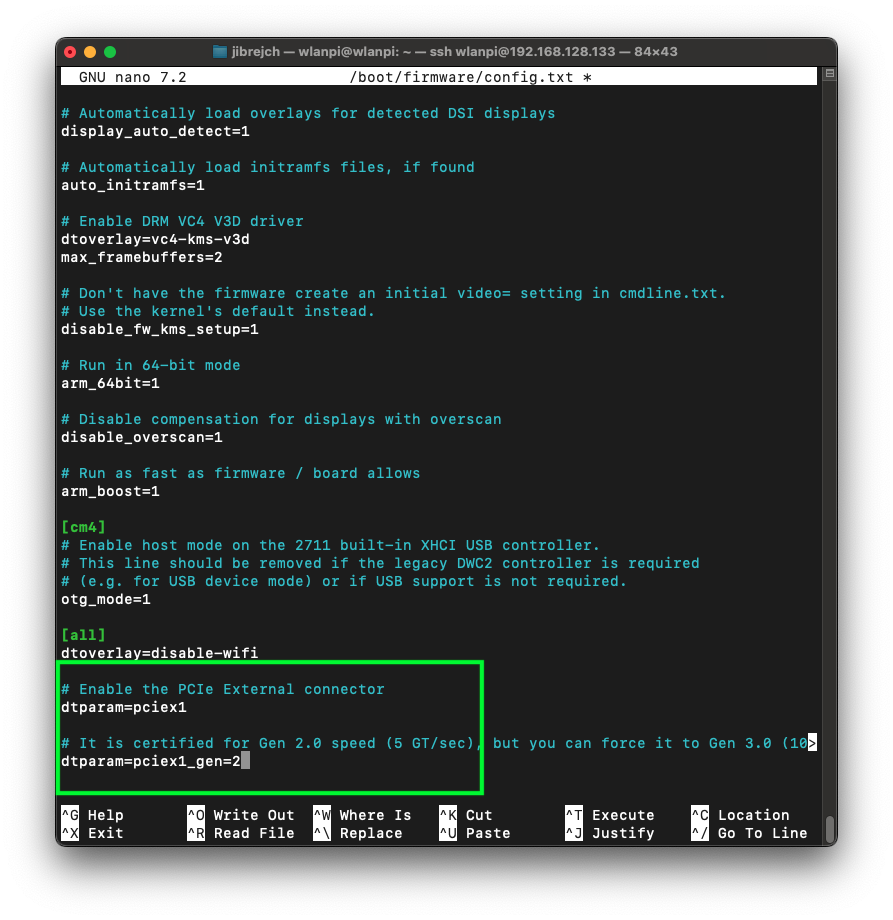
First things first. We need to enable the PCIe connector on the Pi.
sudo nano /boot/firmware/config.txt # Enable the port dtparam=pciex1 # Configure PCIe Gen dtparam=pciex1_gen=2
Build custom Linux kernel and include the Aquantia driver module
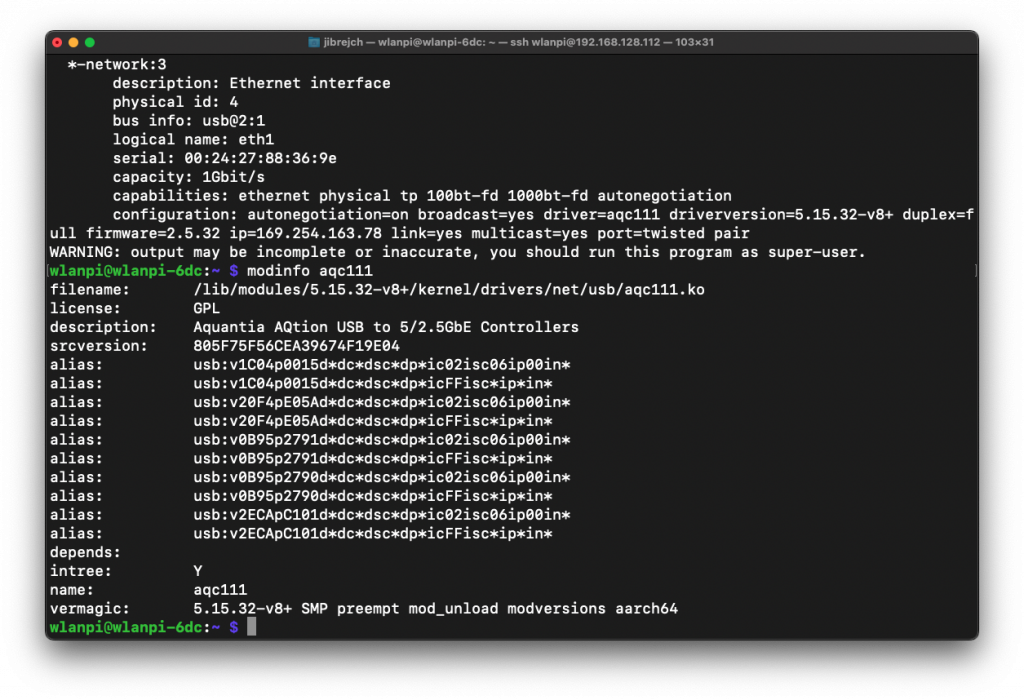
Vanilla Raspberry Pi OS doesn’t include the Aquantia AQC107 kernel module. So we need to burn a micro SD card with a vanilla Raspberry Pi OS Bookworm image, boot the Pi 5 and build a customised kernel.
git clone --depth=1 --branch rpi-6.8.y https://github.com/raspberrypi/linux cd linux/ sudo apt install flex bison aptitude -y sudo aptitude install libssl-dev make bcm2712_defconfig
Edit the config file:
sudo nano .config
Add these 2 lines to .config file:
CONFIG_AQTION=m
CONFIG_AQUANTIA_PHY=m
Trigger customised kernel build on the Pi. This will take some time, so bear with us, please.
sudo make -j4 Image.gz modules dtbs
sudo make modules_install
sudo cp -v arch/arm64/boot/dts/broadcom/*.dtb /boot/firmware/
sudo cp -v arch/arm64/boot/dts/overlays/*.dtb* /boot/firmware/overlays/
sudo cp -v arch/arm64/boot/dts/overlays/README /boot/firmware/overlays/
KERNEL=kernel_2712
sudo cp -v arch/arm64/boot/Image.gz /boot/firmware/$KERNEL.img
uname -a
sudo reboot
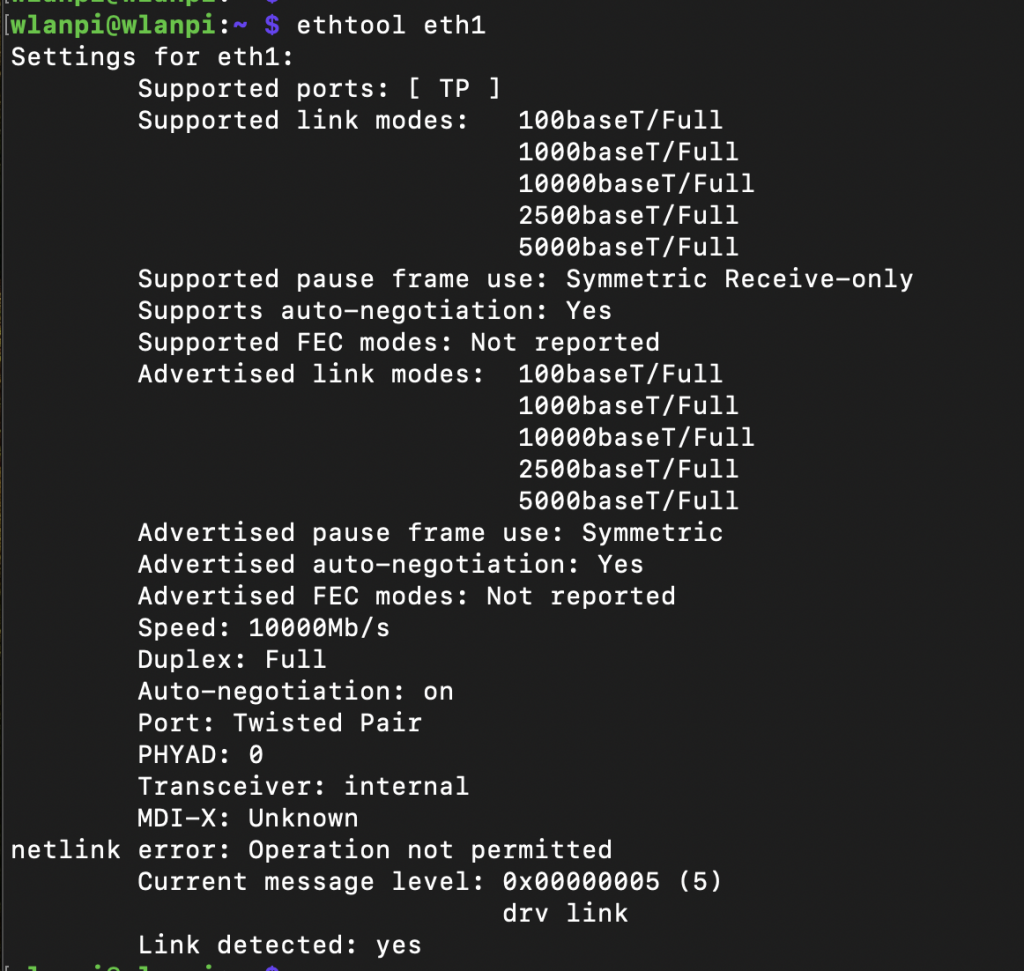
After reboot, the LED light on the network adapter should come to life and we can capture first impressions.
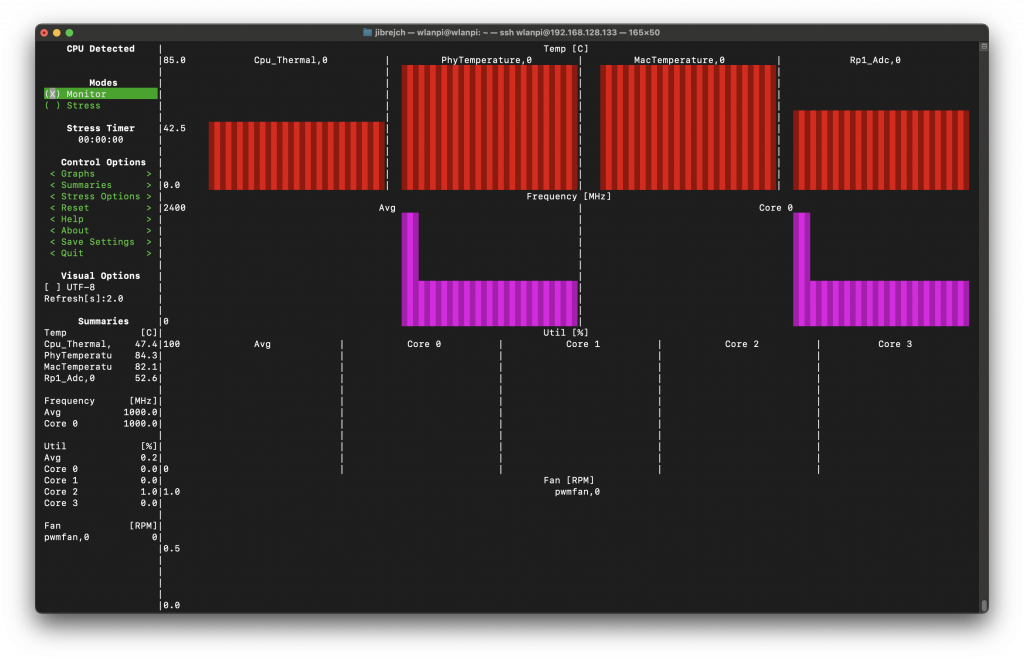
Temperature
First thing you will likely notice is how hot this network adapter runs. It runs at 85° Celsius in idle which is slightly worrying and you can literally burn your fingers if you are not careful. Thumbs down on the thermal design front.
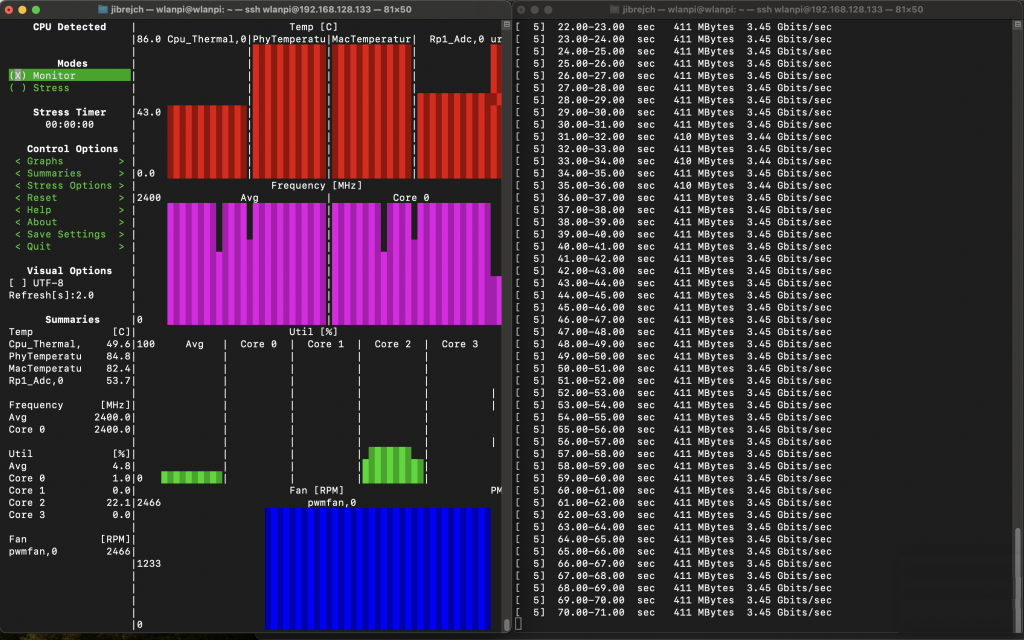
Under load, surprisingly, it ‘only’ runs 0.5° warmer.
How fast can it go then?
Raspberry Pi 5 officially supports PCIe Gen 1 and Gen 2. It is not certified for Gen 3.
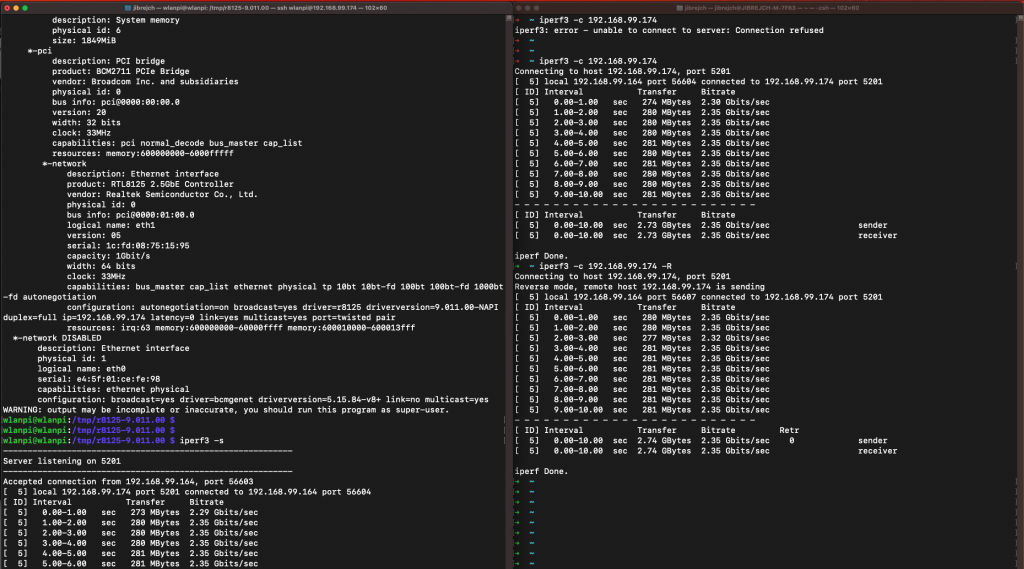
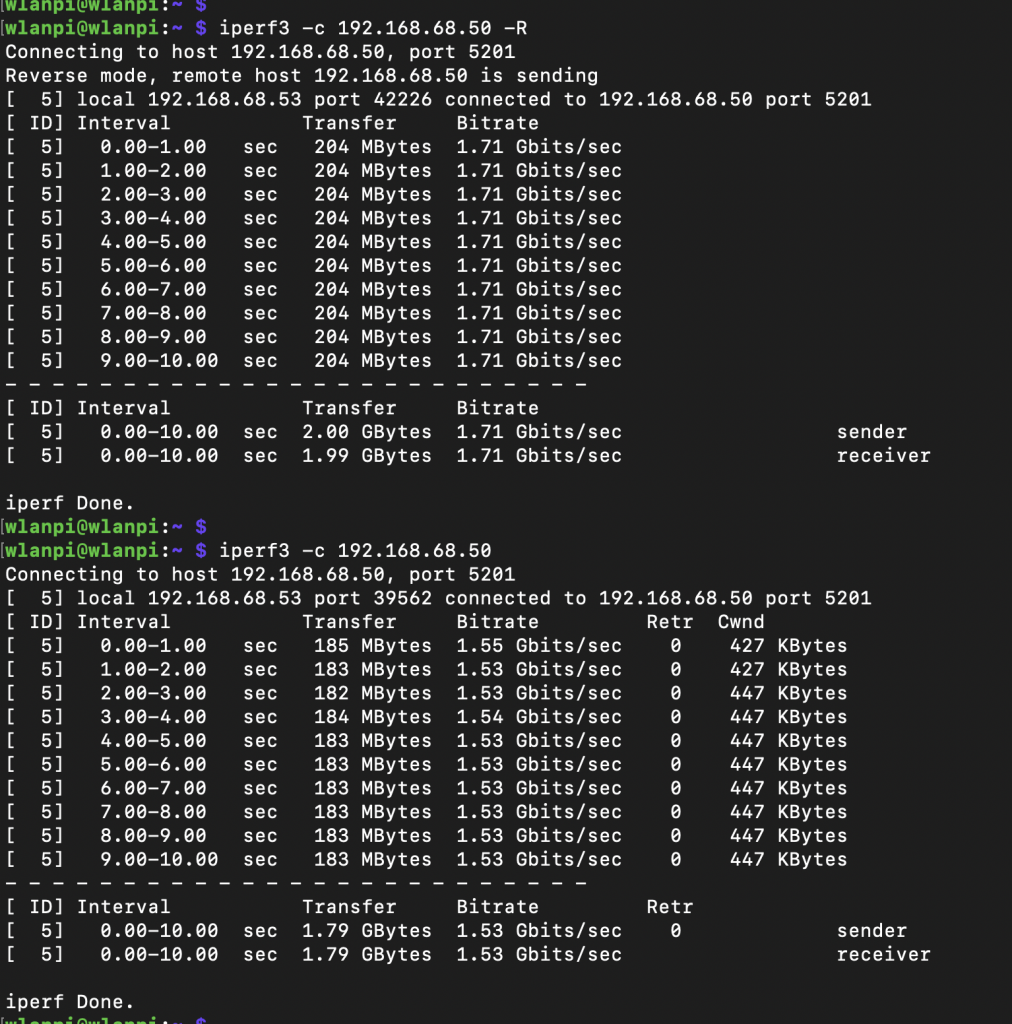
PCIe Gen 1 mode
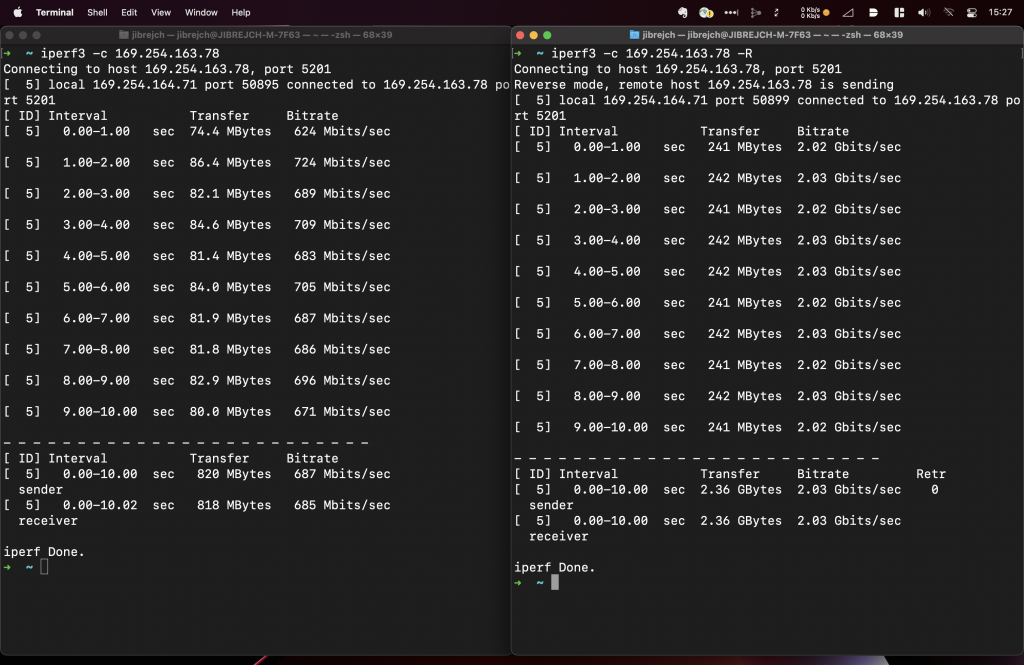
In this slowest mode, I got 1.71 Gbps/1.53 Gbps iperf3 TCP results with standard iperf3 settings. No jumbo frames, no other tweaks.
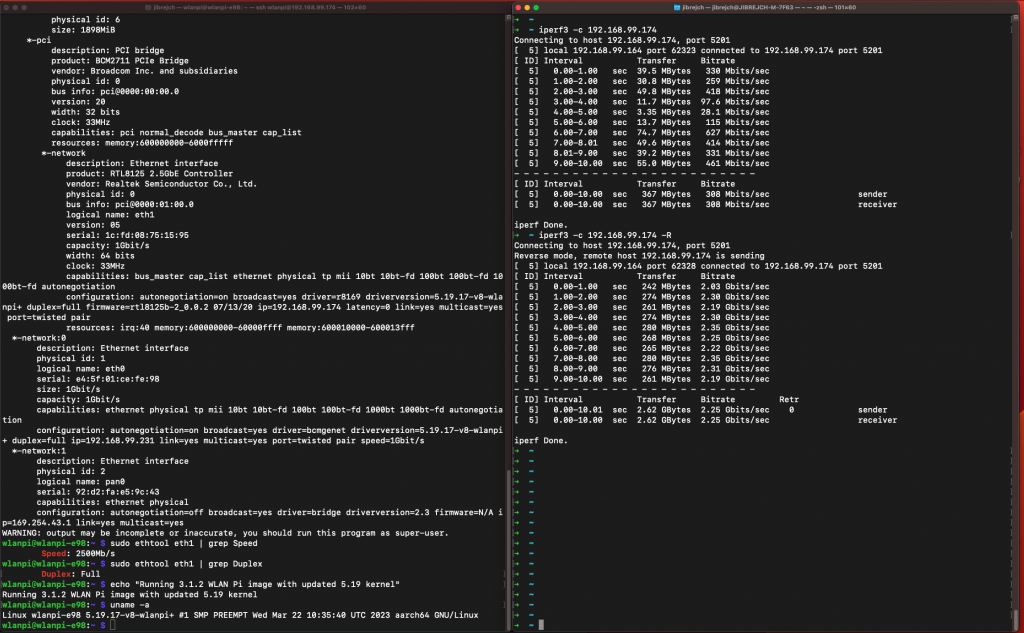
PCIe Gen 2 mode
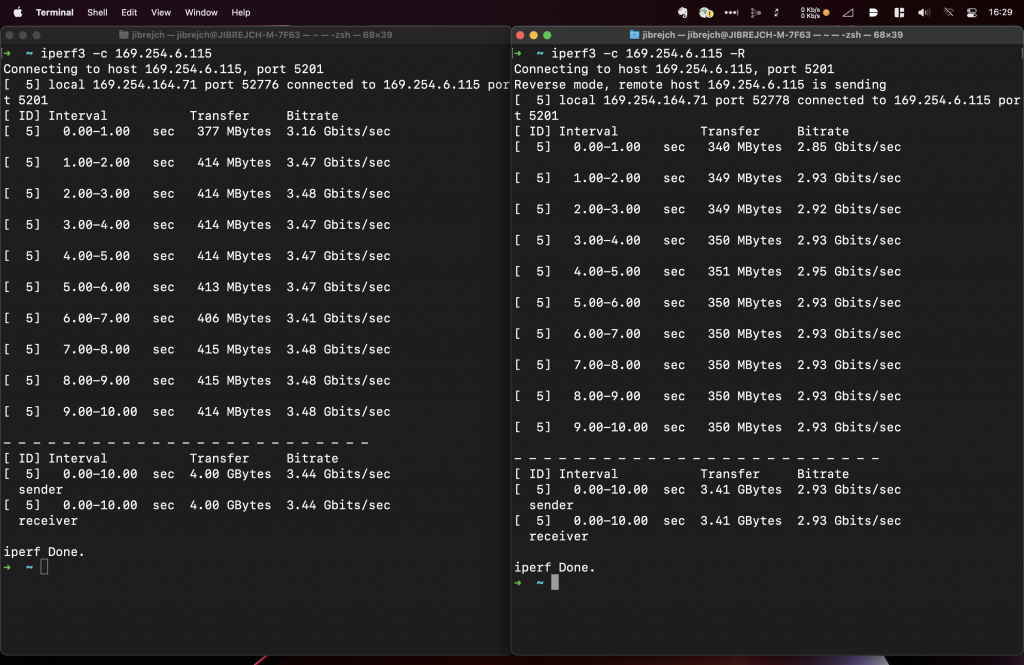
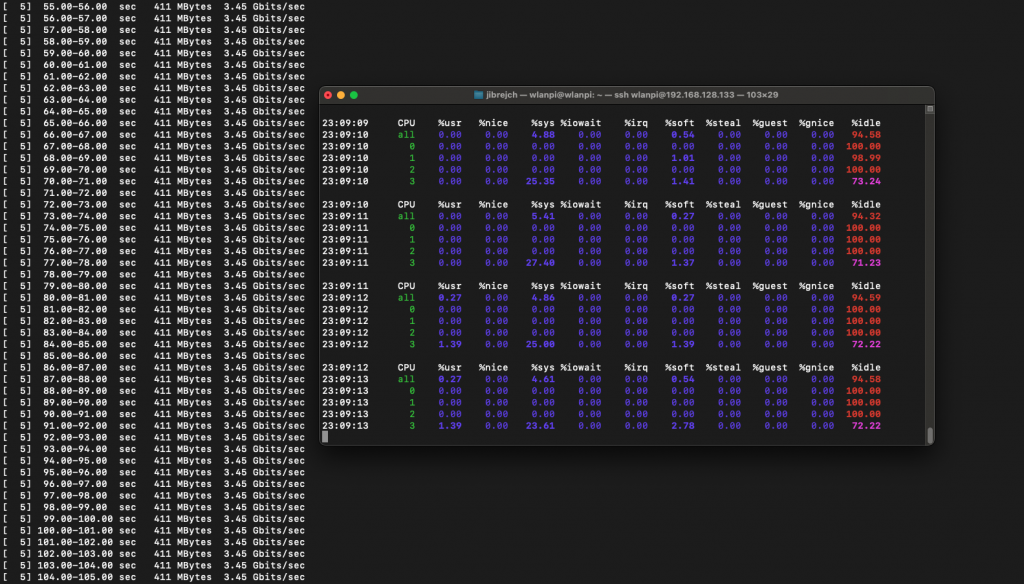
Again, with standard iperf3 settings, I measured 3.44 Gbps/3.04 Gbps TCP throughput between 2 computers both connected to 10 Gbps switch ports via 10 GbE Full Duplex.
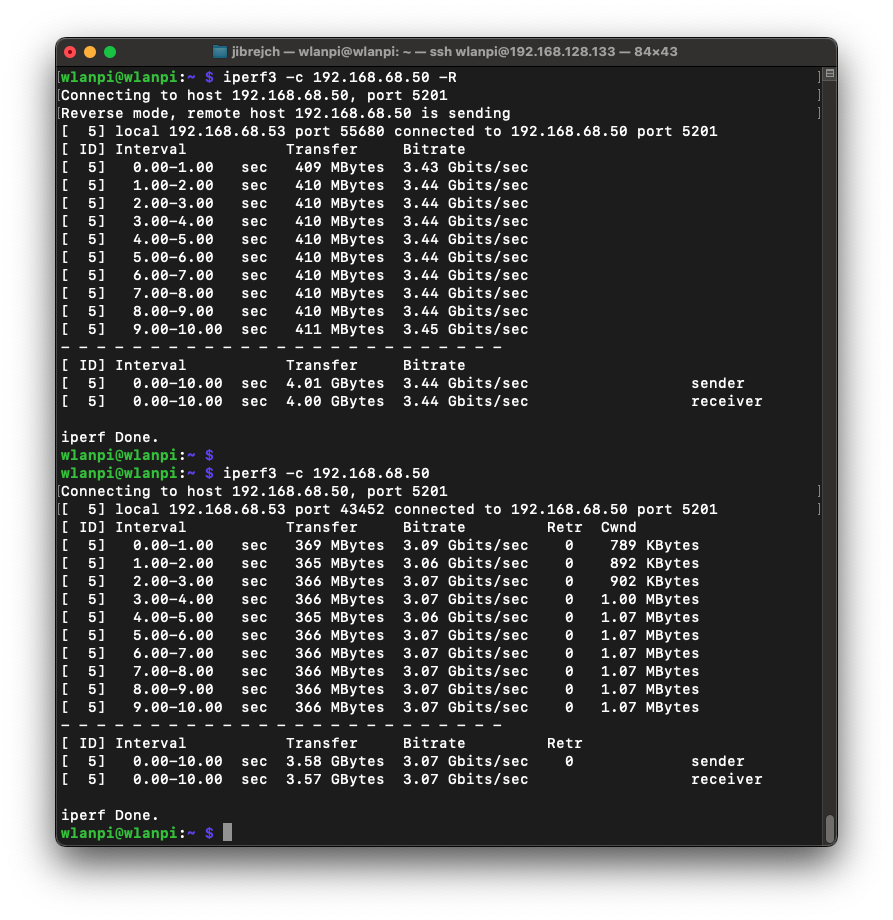
In idle conditions, this setup draws 7.5 W, and 8.9 W under 10GbE adapter iperf3 -R load (3.45 Gbps). Using more iperf3 parallel streams (the -P parameter) did not help at all.

PCIe Gen 3 mode
The adapter supports PCIe Gen 3, but it doesn’t work with the Pi. The Pi is not certified for Gen 3, so I can’t say anything bad about this. The Ethernet adapter is not recognised in Gen 3 mode, and no interface is present in ip a. Sometimes the Pi will fail to boot.
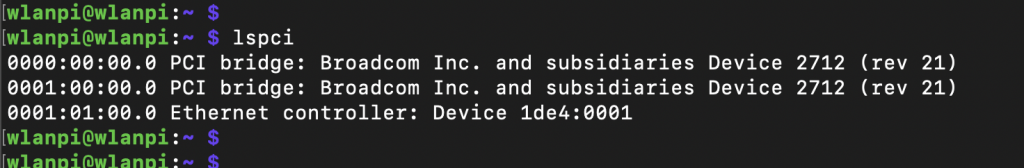
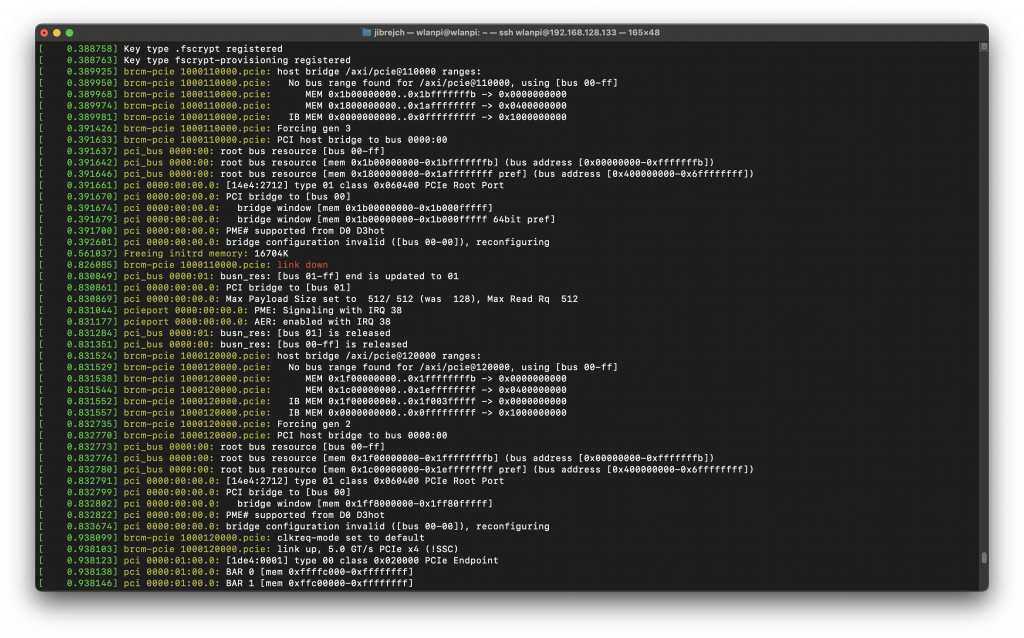
According to dmesg, the Pi forced Gen 2 mode:
brcm-pcie 1000110000.pcie: link down brcm-pcie 1000120000.pcie: Forcing gen 2
I powered my Pi from M2 MacBook USB-C port. So I thought, I might be running into under-voltage issues. I tested the official Raspberry Pi 27 W (5 V * 5 A) AC power and it made no difference.
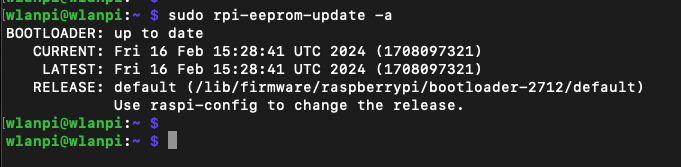
Did you upgrade Raspberry Pi 5 firmware?
Yes, I did. It is running the latest version available as of March 2024.
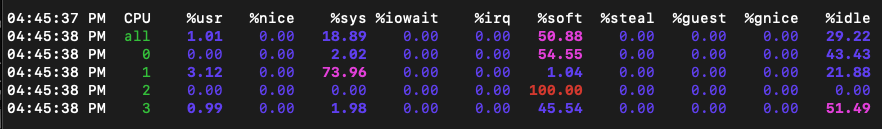
Low CPU utilisation
One feature I really enjoyed is the extremely low CPU utilisation under load. I saw slower 2.5 GbE adapters hammer CPU with interrupts, but that’s not the case for this NIC. AQC107 does really good job at keeping the CPU cool.
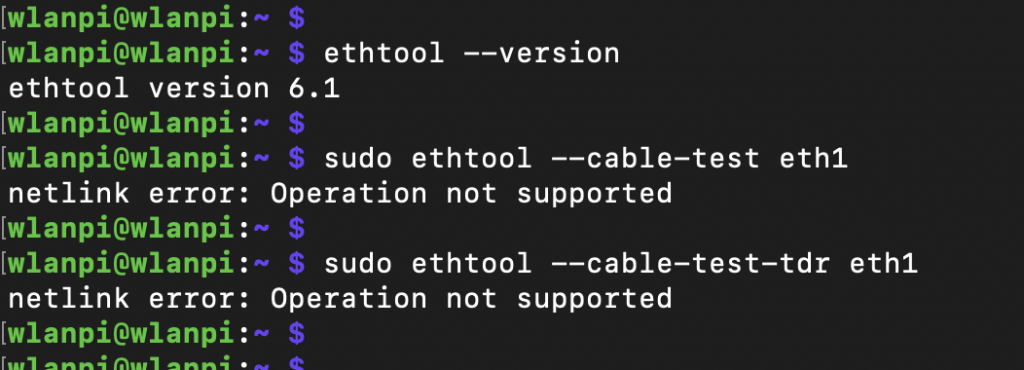
Cable analytics
Marvell supports Cable Diagnostics feature which uses TDR to measure cable length and detect Ethernet cable for defects. Unfortunately, it doesn’t seem to be supported on the AQC107 chip.
Can you get 10 Gbps out of this adapter at all?
I am glad you asked. How does an Intel NUC with this 10 GbE adapter sound? I’ve just tested it, here you go.

Summary
The high operating temperature really makes this adapter something I can’t recommend. With maximum throughput below 3.5 Gbps, I think you would be better off choosing a 2.5 Gigabit Ethernet adapter, which runs cool and delivers 2.35 Gbps/2.35 Gbps throughput.
Have you tested any other 10 GbE adapter? Did you get better results? Did you find any 2.5 Gbps Ethernet adapter that supports Cable Diagnostics? I am all ears.
Special thanks
Thanks to Luke Jenkins for exploring and sharing the kernel build instructions. Also, thanks to the WLAN Pi team. You can buy the team a coffee using this link.