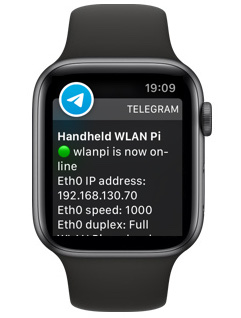
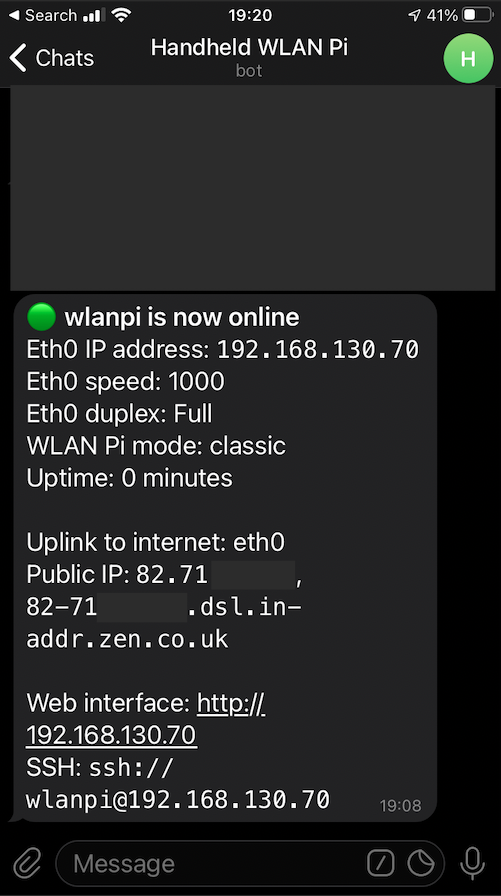
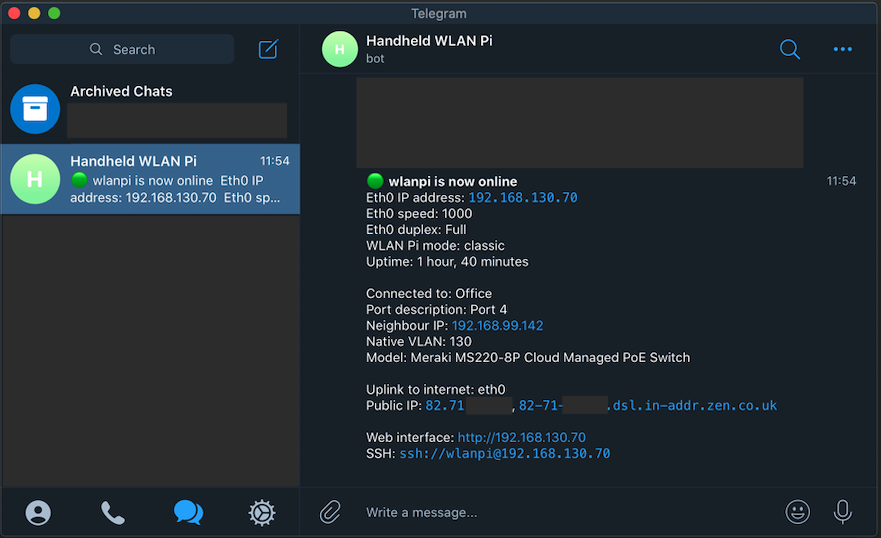
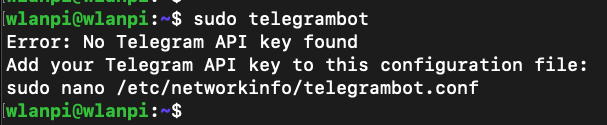
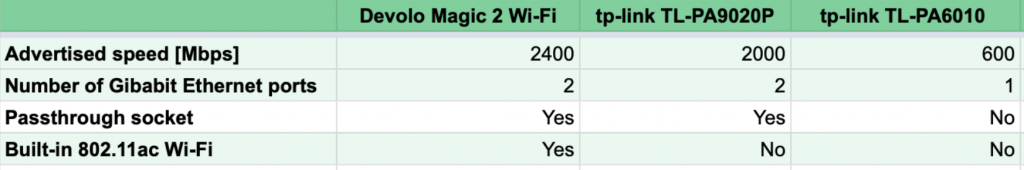
Sabrent NT-SS5G is a 5 GbE USB adapter, which allows you to achieve higher throughput than 2.5 GbE adapters, and break the 2.35 Gbps barrier. It works great on Windows. If you are a macOS or Linux user, I recommend you consider other options like this instead.
The adapter itself is larger than 2.5 GbE adapters, it uses AQC111U chip, and ships with short 2 detachable USB-A and USB-C cables. USB-C port on its back connects the adapter to your computer. A metal shell protects it, serves as a heatsink, and also adds to its weight.

Windows 11
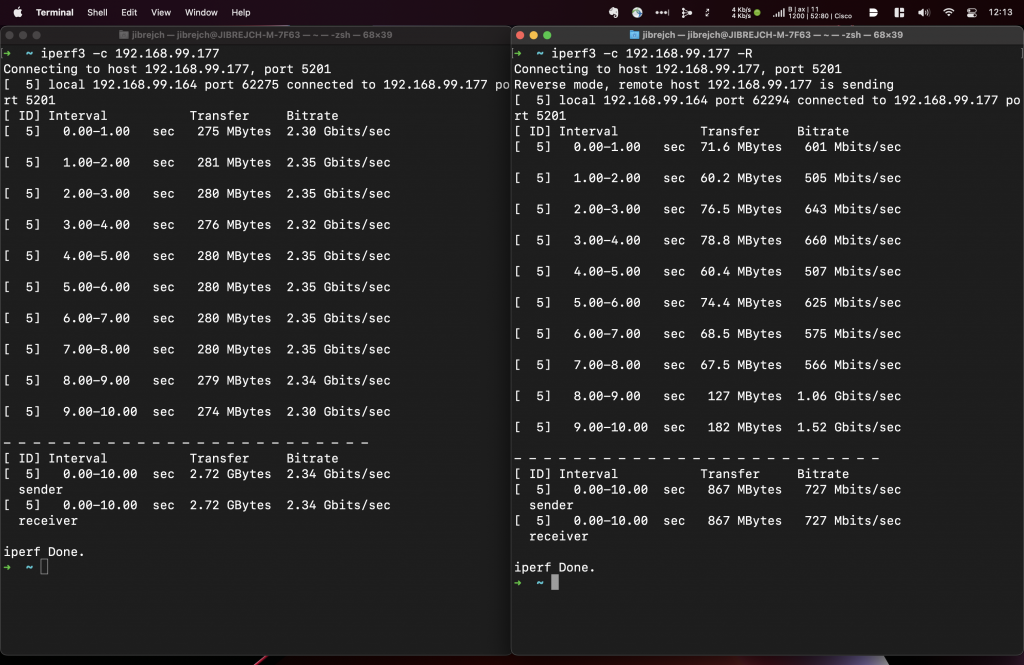
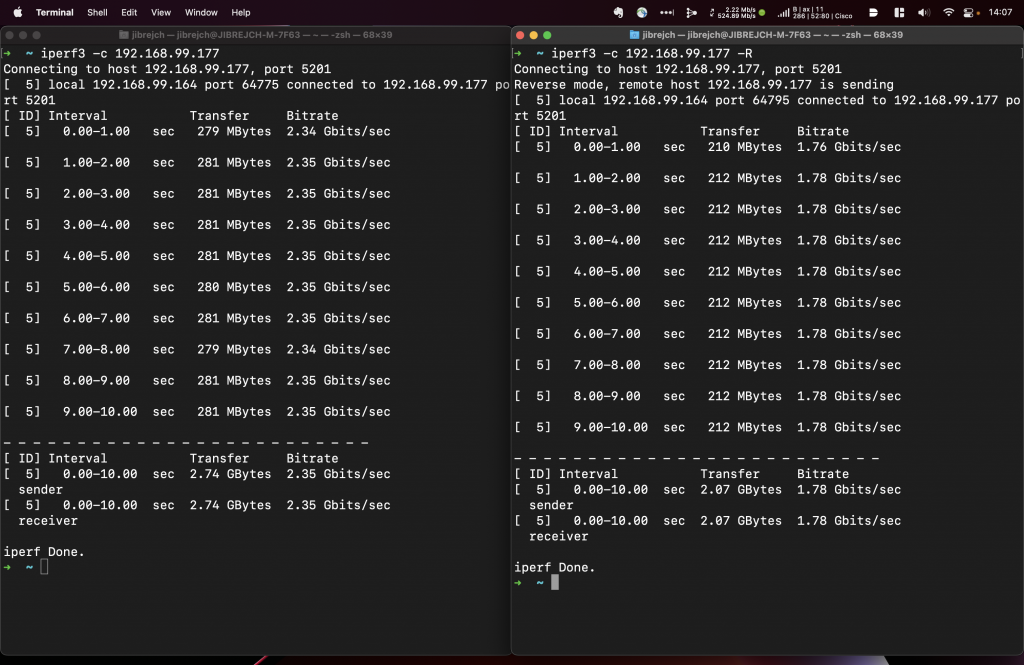
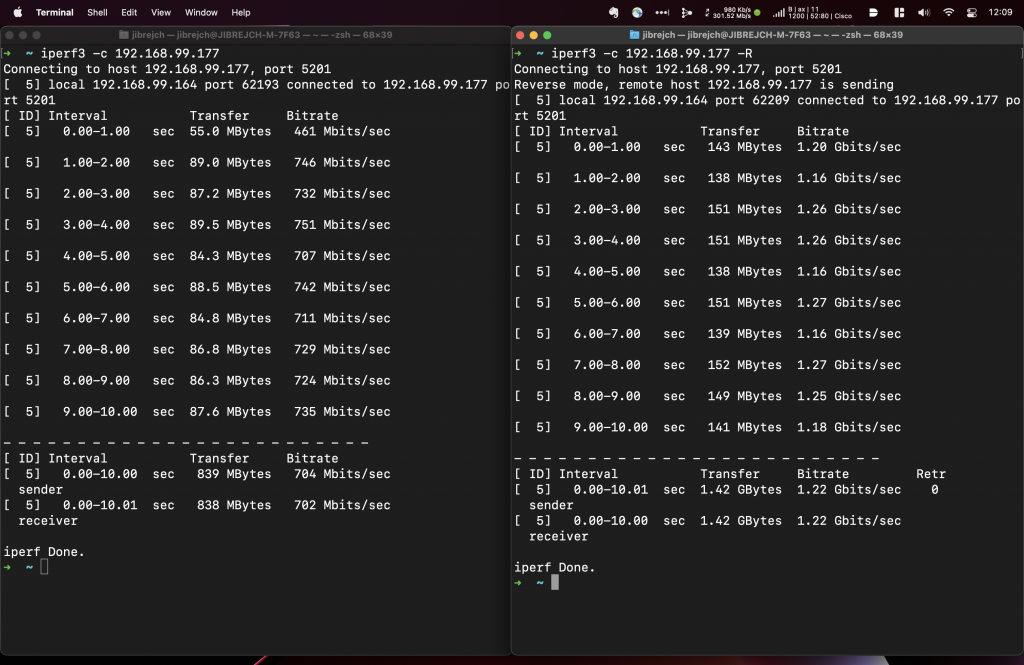
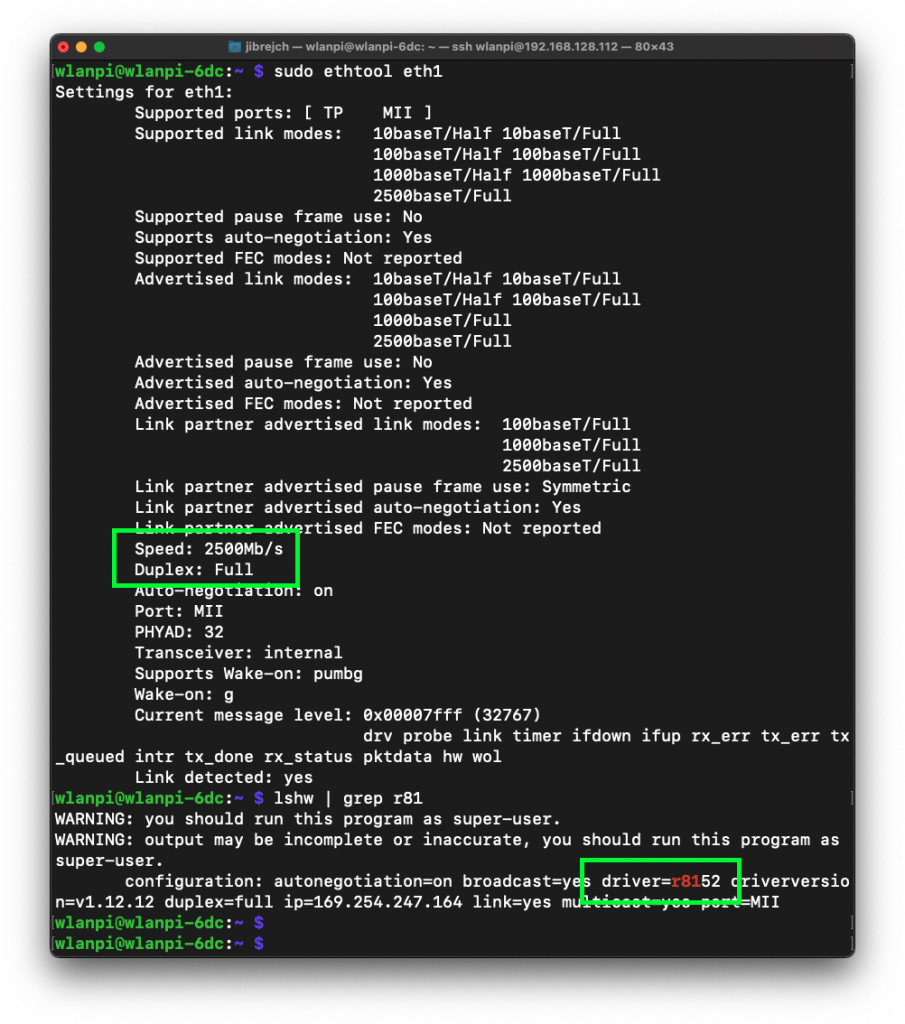
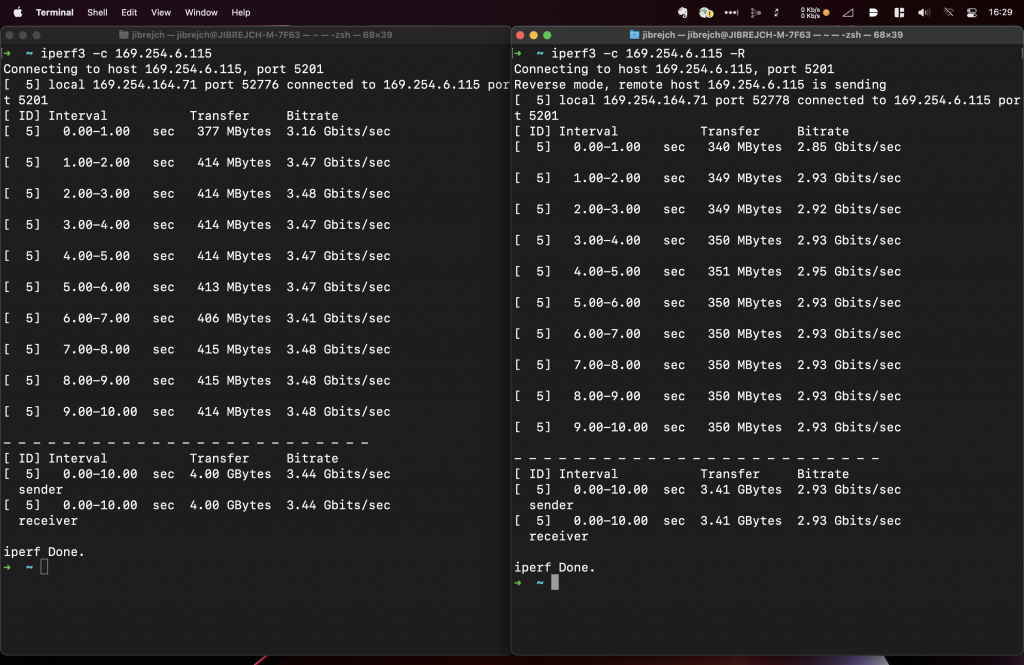
Install the driver from Sabrent’s website and you are good to go. In my tests with this Topton M6 Mini PC, I measured 2.93 Gbps down and 3.44 Gbps up with default iperf3 settings.

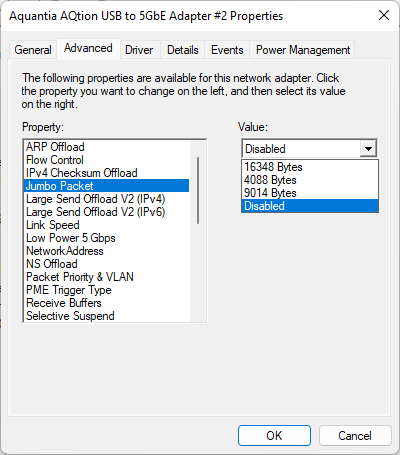
In adapter options, you can actually configure quite a few things including Jumbo frame support. Note that these are fixed values.
macOS
I can’t recommend this adapter for macOS users. It forces you to disable macOS System Integrity Protection (csrutil), otherwise it won’t work. It might be okay for a proof of concept or lab setup, but I would hesitate from using it in production.
This is how to install the driver if you were interested:
- Install the driver using the pkg file provided by Sabrent. It installs a Kernel Extension (kext), which drives this adapter.
- Enable the extension by going to
System Preferences > Security & Privacy > enable the extension > Reboot. - After reboot, unplug the adapter and plug it back in.
- It should work as long as you leave the System Integrity Protection disabled.
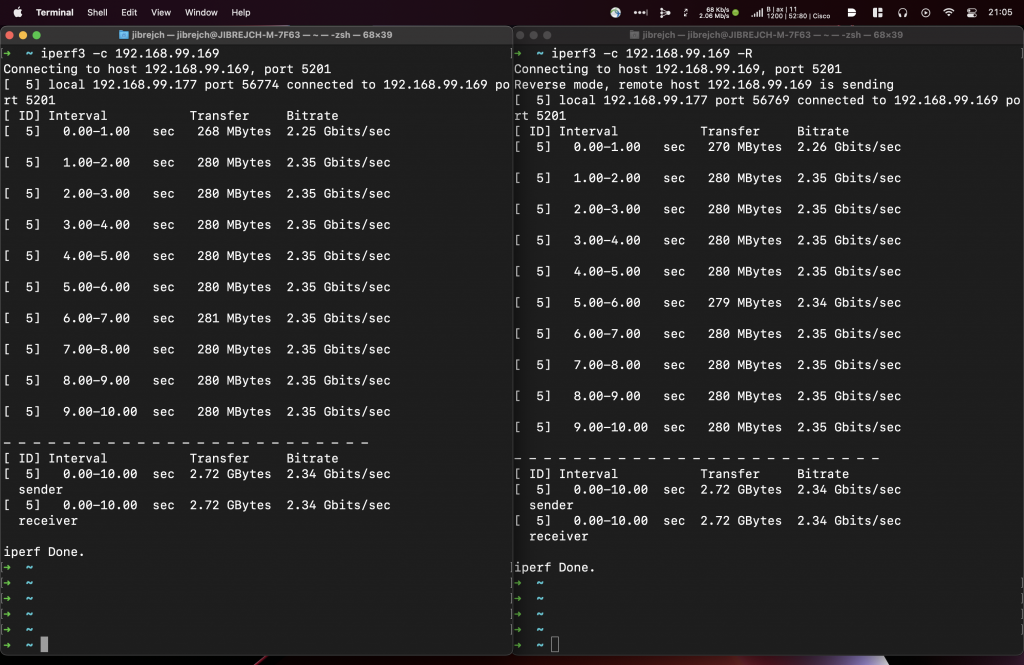
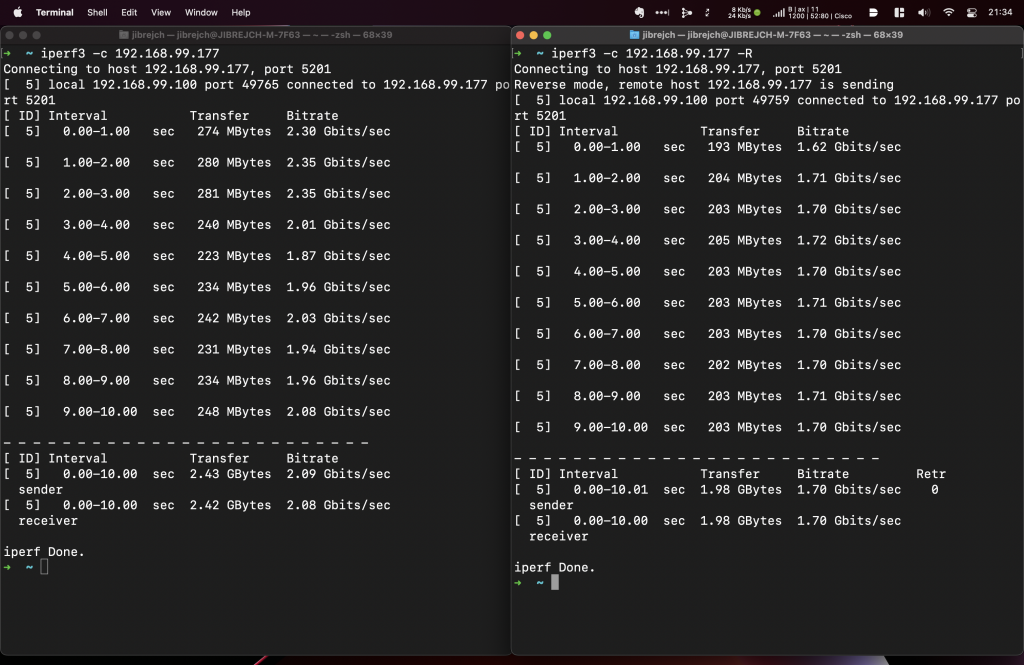
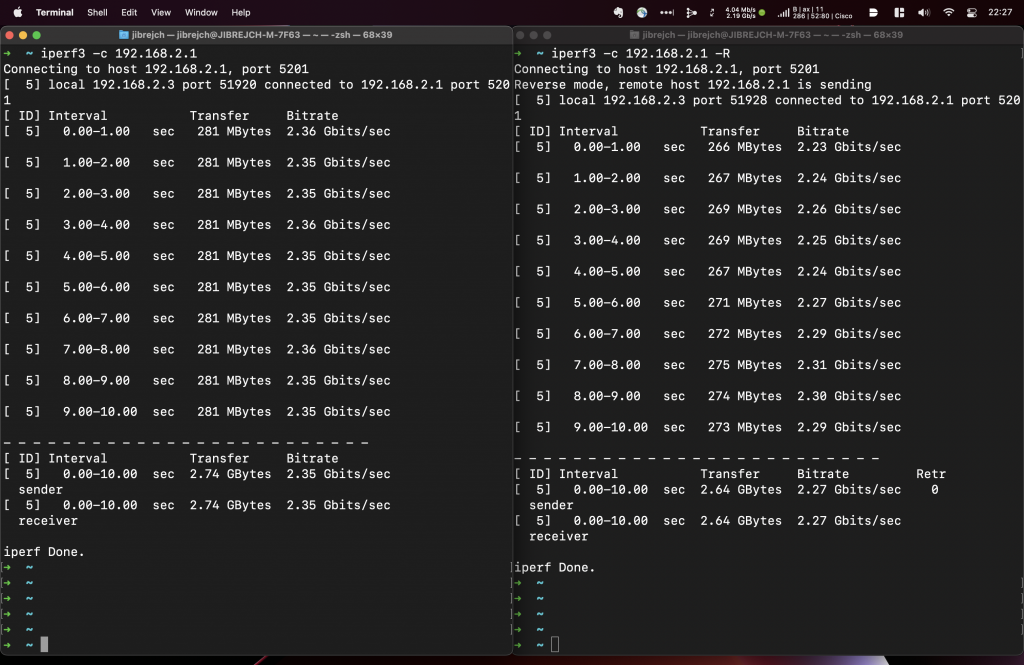
From throughput perspective, it saw download speeds of 3.30 Gbps, and upload of 3.45 Gbps. This was with default iperf3 settings, standard 1500-byte MTU and one stream. Great results considering that this adapter’s USB interface maximum theoretical throughput is 5 Gbps.
In my view, you might be better off buying a 2.5 GbE adapter, which can push 2.35 Gbps up and down consistently and with no driver installation needed. I tested one here. Alternatively, a 10GbE Thunderbolt Ethernet adapter is even faster choice, but more costly, and larger form factor. Or, if your other half approves, treat yourself to an M1 Mac Mini with built-in 10 GbE 😉
Linux
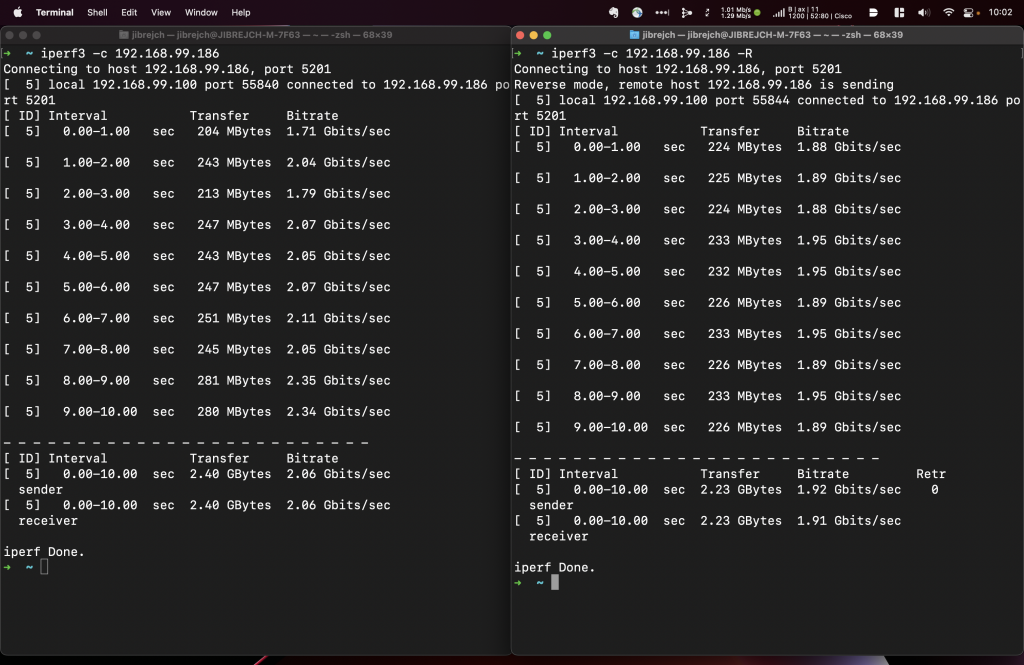
I tested this adapter on 64-bit Raspberry Pi OS running on Raspberry Pi 4. Although the default driver distributed in Linux Kernel 5.15 works, it doesn’t even deliver symmetric 1 Gbps.

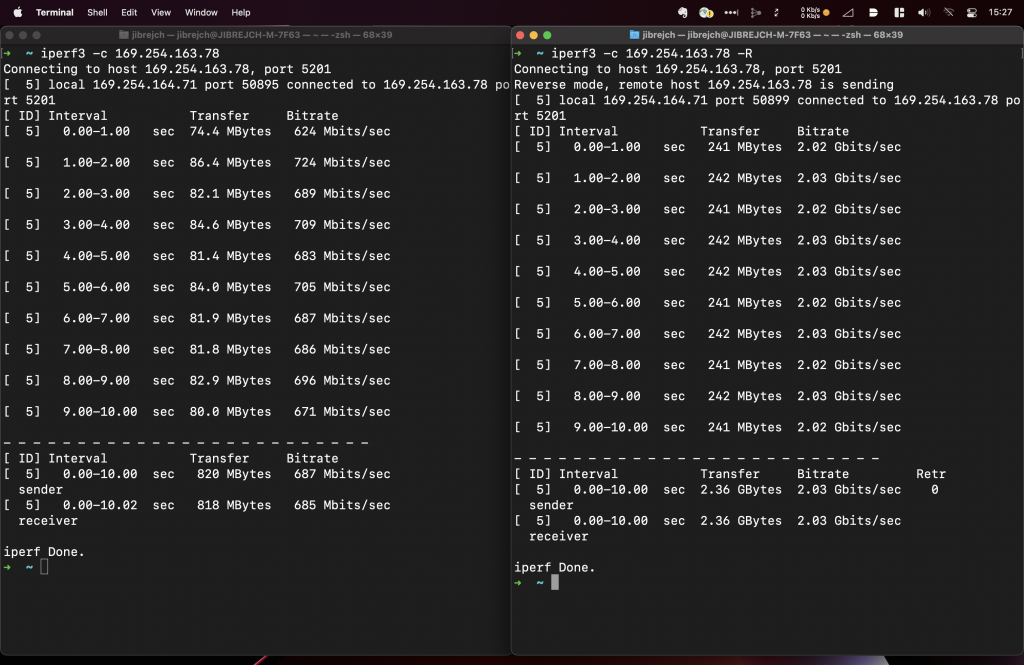
Let’s download the latest driver from Sabrent’s website. Unfortunately that doesn’t seem to be able to compile for 64-bit OS. I tried compiling on 32-bit Raspberry OS, to no avail. If you have any ideas, please do let me know.
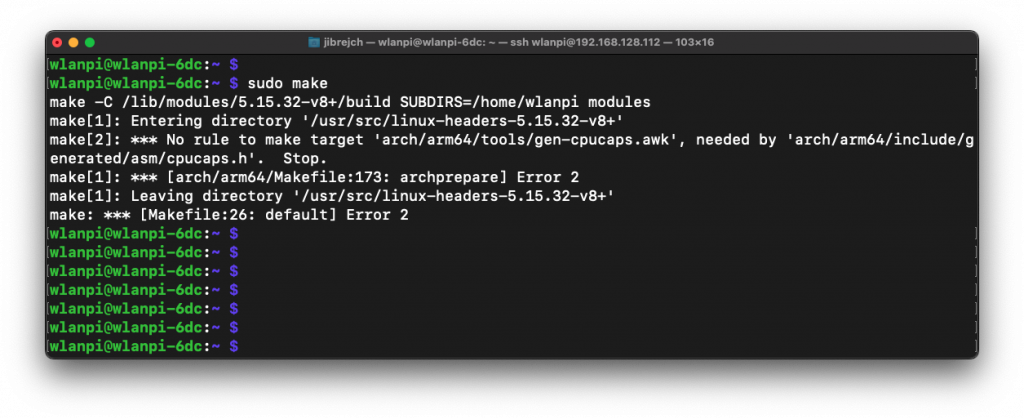
So, on Linux, a Realtek RTL8156B based 2.5 GbE adapter might be a better choice for you. Here is the one I tested.